Revolutionary protection for
Company Intranets
Security for today and tomorrow
Maintaining data protection is one of the greatest challenges companies are facing today, because no one wants to risk a bad image due to media reports of data having been stolen from the company. Yet companies are still concentrating on protecting themselves from access from outside the company, although statistics have repeatedly shown that a large part of the spying is taking place from the local network. This is where a maximum of protection is needed that can be implemented with only a minimum of effort and without interrupting internal workflows.
Network Access Control (NAC) solutions support the company in this task. The ARP-GUARD solution, in particular, can be implemented easily and quickly because it requires no changes to existing network structures. It learns on its own which devices are on the network, and produces a graphic overview of the network including all existing switches and routers.

RELIABLE PROTECTION
EASY INTEGRATION
CENTRAL MANAGEMENT
Software modules

Network Access Control

NAC & VLAN management

Layer 2 IPS & NAC

ALL in One
ARP-GUARD - the secure protection for your network
ARP-GUARD gives you complete access control for your network! New devices that are connected to the network are detected and reported in real-time. The devices are uniquely identified using the MAC address or certificates (802.1X). Additional fingerprints that are created when training the devices increase the security level.
ARP-GUARD thus makes protected and controlled access to the network possible. You decide how to deal with unauthorised devices with user-defined or company-specific rules found in access and security guidelines. These guidelines can range from notifying the administrator by email to automatic defence against unauthorised devices or relocating to special quarantine or guest VLANs.
Controlled and secure access to IT networks
Virtually all internal company information can be accessed over your local network. Highly sensitive data vital to your company! Formulas, design plans, contracts, patents.
ARP-GUARD makes sure that users don't use any unauthorised notebooks, smartphones or even wireless access points. Our software solution protects your IT infrastructure from malware-infected external devices and your intellectual property from unauthorised access! Our security solution provides reliable protection against unauthorised access to the internal LAN and WLAN, as well as the Internet. With ARP-GUARD, only authorized devices are granted access to your network! Protection of your network takes place in real time, as does network monitoring, localization, and the identification and verification of newly connected devices.
Unambiguous identification of a device is a must. The MAC address or certificates (802.1X) are available here. The ISL proprietary fingerprint process also offers an identity check of the devices at the highest security level. You can combine these security mechanisms to define your own level of security. The unique and individually scalable sensor management architecture makes it possible to secure your company across sites no matter if you are a medium-sized company or a large corporation. ARP-GUARD functions independently of any vendor. You don't have to standardise or even replace your existing infrastructure. ARP-GUARD sees itself as a watchdog and observer of your network that enforces your centrally defined rules, i.e. your security policy, throughout the company.
The ARP-GUARD variants
ARP-GUARD's architecture is designed such that it can be used by small, medium-sized as well as large companies. Regardless of the company's size or what its need are, there is only one management level from which ARP-GUARD is centrally configured and operated. Depending on need, sensors can also be implemented for load balancing or for managing external areas.
Hardware Appliance
The long-standing partnership between SECUDOS and ISL has resulted in purpose-built appliances for ARP-GUARD - bundles comprising field-proven hardware from SECUDOS and the ARP-GUARD software from ISL. These appliances are shipped with ARP-GUARD software pre-installed which means they can be put into operation more quickly. No installation work (operating system, drivers, etc.) is required.
Virtuelle Appliance
The virtual ARP-GUARD appliance (AG-VIRT) was developed in collaboration with our technology partner, SECUDOS. The virtual appliance is based on the DOMOS4 operating system and is shipped with a pre-installed instance of ARP-GUARD. Commissioning takes place intuitively via a graphical user interface and takes about ten to fifteen minutes to complete.
ANY QUESTIONS? WRITE US!
ARP-GUARD Fingerprinting
The experts at ISL GmbH have already developed a fingerprinting tool for ARP-GUARD which searches for keys/certificates on end devices and downloads them to its database, where they are stored as reference values. Afterwards, when an end device is actively connected to the network, one of its public keys or certificates is fetched and compared with the reference value in the database. If the values differ, the device is removed from the network. In principle, fingerprinting, like 802.1X, is susceptible to session hijacking. The difference here, though, is that it's possible to check for compliance with other conditions (based on IP addresses, for example). For end devices with no cryptographic methods, simple fingerprints with specific device properties can provide a level of security far exceeding that offered by MAC address checking.
Fingerprinting is implemented in ARP-GUARD itself and has been activated in many corporate networks, including the networks of 80 Sparkassen (savings banks) in Germany for whom high levels of security is of paramount importance.

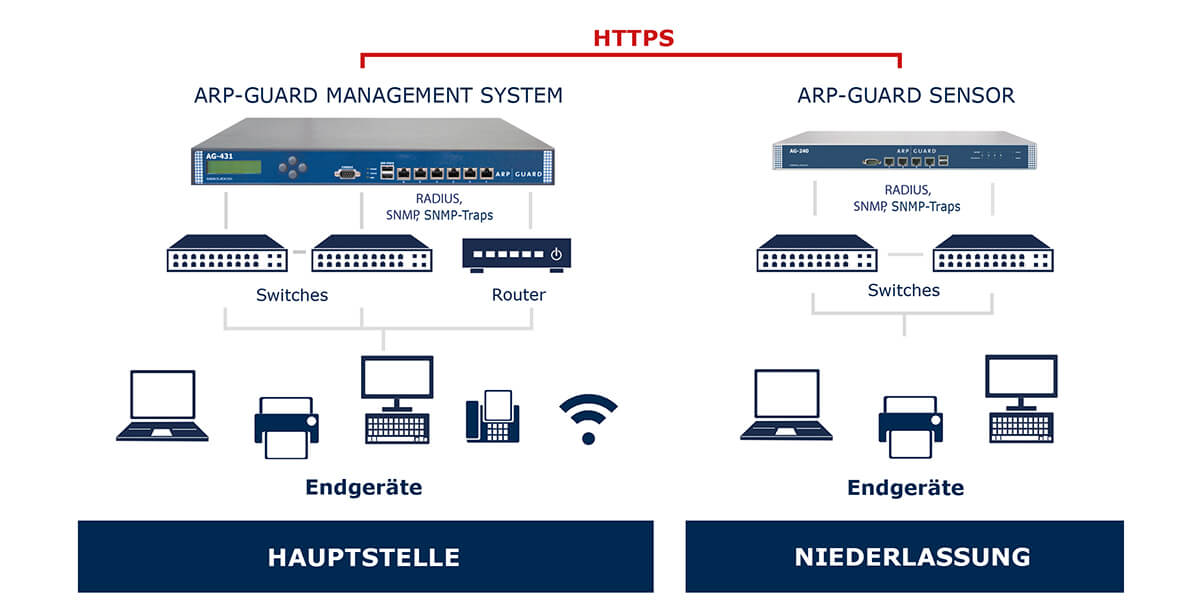
Example structure with ARP-GUARD sensor


 English (UK)
English (UK)  Deutsch (DE)
Deutsch (DE)