
Get the files on the right track to the desired destination
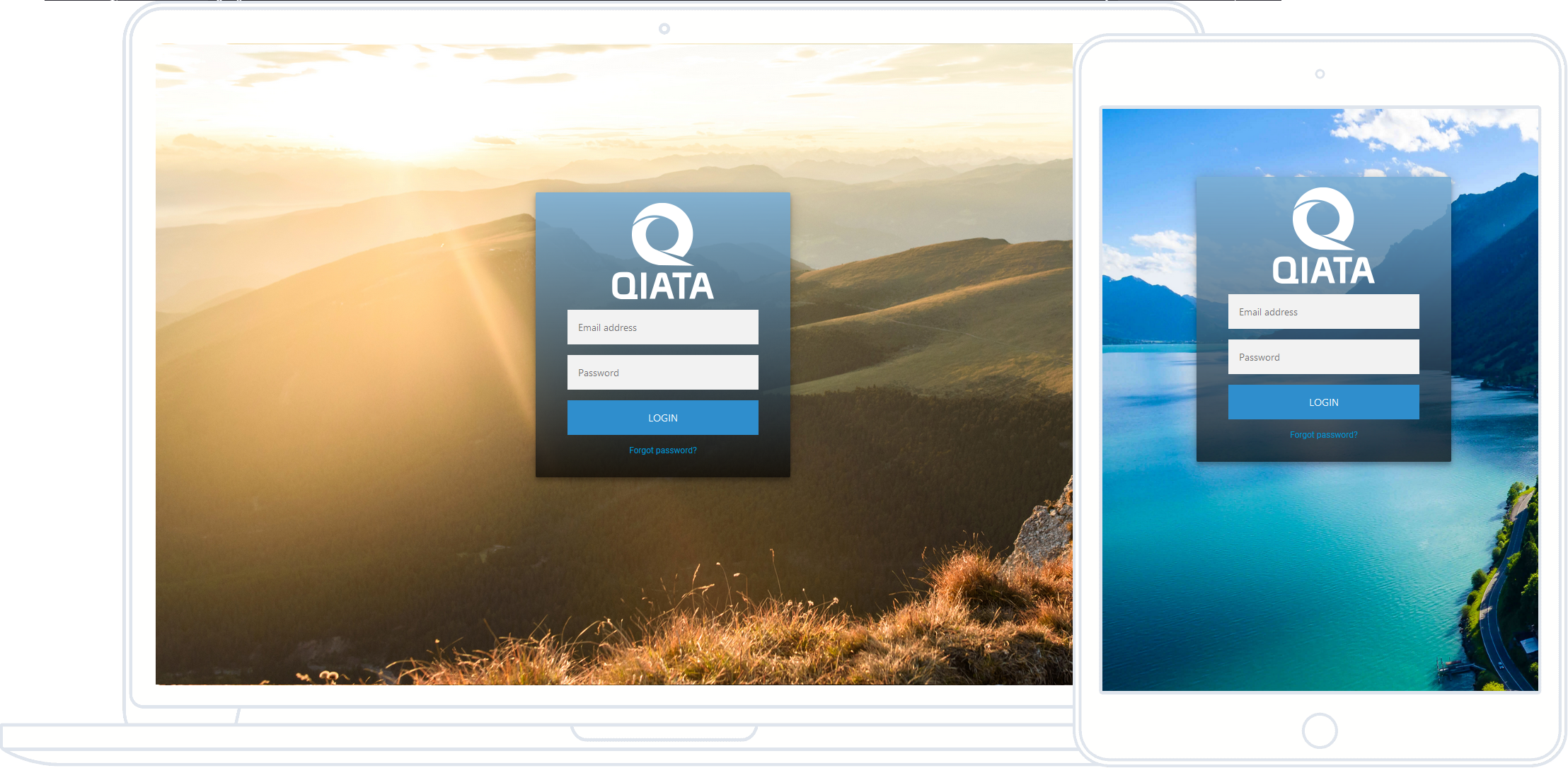





Data in Motion - What does this actually mean?
What are DIMo's?
Working with those is not a big deal as long as it happens inside the enterprise network, but what if the data needs to go “outside”?

The problem
- Often lack of security during transmission
- Sending and receiving larger files
- Missing traceability over reception
FTP
The problem
- Increased administrative overhead
- Missing traceability of access
- Missing ease of use
- No automatic workflows
Cloud
The problem
- Intransparent data protection (GDPR)
- Missing compliance
- Depending on the provider
Download free section guide now
3 reasons that speak for Qiata

EASY

SECURE

COMPREHENSIBLE
File exchange with Qiata
- Send any file type and folder structure securely via Outlook AddIn, DesktopClient or web interface
- Use the invite function to receive files from external parties*
- Using a personal storage space to store files and folders via DesktopClient, WebUI or network drive*
- ...
*Functional right restrictable by administrator
- Easy user and group management*
- Creating policies*
- Creating group administrators*
- Creating approval processes and workflows*
- Creating and configuring archives and backups*
- ...
- Creating Administrators
- Creating group administrators
- Creating policies
- Creating auditors
- Creating approval processes and workflows
- Viewing activities of Qiata users
- Authorization assignment of administrators
- Creating roles / administration roles
- …
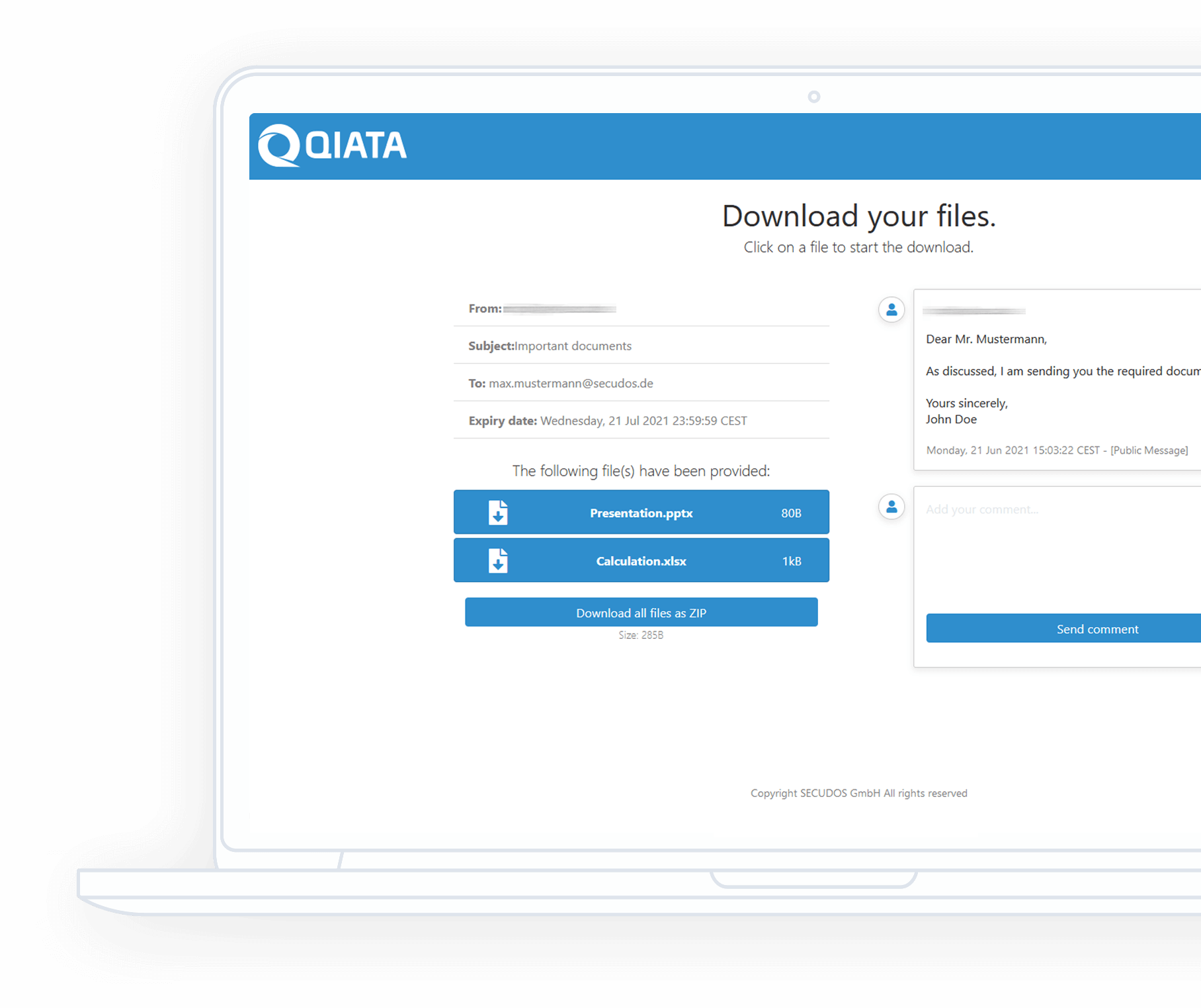
PersonalSpace - Your personal storage space
PersonalSpace is a MultiSpace module of our multifunctional edge application Qiata. The idea behind PersonalSpace is to enable companies to provide their staff and partners with a separate, personal storage space. Thanks to the PersonalSpace function, all authorized users receive an individual space for data storage that cannot be viewed, used or changed by any other user.

Learn more about PersonalSpace now
TEAMTransfer - Working in a TEAM worldwide

Meet this challenge!
With the TEAMTransfer module of Qiata you take this hurdle quite easily. Each participant can upload their files to a secure "pool" on the Qiata and provide internal as well as external participants. Of course, everything is as secure and traceable as you already know it from Qiata. In addition, invitation functions, read-only settings and comment functions round off the circle of numerous features. Moreover, TEAMTransfer is kept simple and intuitive as possible. Extensive training is not required.
Learn more about TEAMTransfer now
Open ID Connect - Connect your ADFS or AzureAD
The Open ID Connect standard is based on the OAuth 2.0 protocol and inherently offers a high level of simplicity and security. For example, OIDC can also be used to create an end-to-end single sign-on experience for users by allowing them to log into Qiata once and then remain in their session. The length of this SSO session can be defined by the admin. This also applies to the Secure Desktop Client (SDC), for example.
Learn more about OIDC now
5 ways to use Qiata
You decide for yourself!

Webbrowser
Mail-Client


API interface
Outlook Plug-In
SECURE Desktop Client (SDC)

Securing Transfers & Accounts
Most users know that passwords are very important nowadays, but many still neglect to take the necessary care. They store their passwords incorrectly and in many cases do not choose the necessary complexity. This makes it particularly easy for cyber criminals. To reduce the risk, there are several methods available today. One of them is two-factor authentication. Instead of a single password, users must enter another authentication feature to complete authentication. This second factor ensures that the login attempt is really made by the user. Such a second factor can be the mobile phone, for example. In case of doubt, physical access to the cell phone should only be possible for the specific user. Especially when transferring security-critical files, as it is the case with Qiata, appropriate security is important.
We accompany you on the way to your digital sovereignty!
Global digitization is unstoppably on the rise. In order for a company to remain efficient and productive on a successful footing, it is essential to achieve and maintain digital sovereignty. Appropriate solutions must be able to demonstrate attributes such as simple handling, security, user-friendliness and flexibility in use. The three essential attributes of IT security - confidentiality, availability and integrity - are the basic building blocks. All this implemented reliably and professionally in a single solution? Qiata shows you how!
The multifunctional edge application Qiata encompasses all of the above features in an uncomplicated layout. Secure, simple and always traceable file transfer without the need for in-depth, technical know-how... for both sender and receiver.

Qiata in detail



 English (UK)
English (UK)  Deutsch (DE)
Deutsch (DE)